 ESDC Security Policy
ESDC Security Policy
4. Policy statement
This Policy outlines the organization’s direction and procedures for all the security control areas outlined in the TBS Policy on Government Security including all of its subsidiary policy instruments, directives, standards, guidelines and technical documentation as well as the Policy on Service and Digital. For effective and efficient ESDC operations, this departmental Policy also supports awareness, open collaboration, and ensures that expectations for security activities within the Department are well-defined.
This Policy is supplemented by:
- ESDC Fraud Framework
- ESDC IT Security Framework
- Departmental Policy on Privacy Management
- ESDC Privacy Management Framework
- Integrity Services Branch Strategy
- ESDC Service Strategy
5. Overview
The portfolio of Employment and Social Development Canada (ESDC) is comprised of a number of supporting entities: the Labour Program; Service Canada; Minister of State for Seniors; and Minister of State for the Status of Women. These entities work in a combined effort in providing services to Canadians, businesses and a number of corporate enterprises with a number of other departments and agencies under the Government of Canada for the social, political and economical stability of the country.
The Department is responsible for security governance and ensuring that security measures are in place to protect its employees, clients, information, and other assets; making sure it is prepared to respond to current and evolving security threats, and ensuring that the management of security is systematically woven into the business, programs and culture of the organization as a whole. In essence to give the organization and Canadians peace of mind and build trust.
As such, to support an important building block of good governance and accountability, this suite of security policy instruments helps the organization to identify security weaknesses at a macro and micro level in order to better manage risk; adequately align and address the requirements of relevant federal legislation; and provide an authoritative reference to ESDC employees on the practice of security management.
6. Objectives and expected results
Objectives
- Provide assurance to stakeholders about the security risk management practices within the Department.
- Support a secure working environment for employees and safe conditions of service for Canadians.
- Enable the timely and consistent management of security incidents and support a high level of readiness for ESDC’s critical services and operations to counter disruptions or emergencies.
- Promote and maintain a department-wide security culture that supports the on-going protection of people, information and assets.
Expected results
- ESDC’s security management and activities supports compliance with regulatory requirements and reflects the complexity, breadth and scope of the organization’s mandate, governance, programs and services.
- Risk-based security measures, practices and controls are documented, applied, monitored and maintained to protect employees, clients, sensitive information and valuable assets from security threats and vulnerabilities.
- The Security Program contributes to business process optimization; strengthens monitoring and reporting; and facilitates the detection and mitigation of internal and external security risks in a measurable and meaningful way.
- The Management of security events/incidents is coordinated; includes real-time analysis; and integrates various approaches in order to allow ESDC to determine and apply effective control measures and adapt to a dynamic threat environment.
- The Department uses modern technology and well-developed strategic plans to coordinate emergency and business continuity efforts; mitigate security threats and vulnerabilities; and recover critical services and operations to appropriate levels during disruptions and emergencies
- ESDC’s security and awareness and training program is managed to strengthen internal security capacity and expertise, and enable the organizations personnel to gain an understanding of security issues and their overall security responsibilities.
7. Requirements
"The Chief Security Officer (CSO) is responsible to the deputy head or to the departmental executive committee to provide leadership, coordination and oversight for departmental security management activities”.
- 2019 TBS Policy on Government Security
7.1 Security governance
A well-managed security program provides assurance to stakeholders that the organization’s collective efforts and overall security posture allows for the protection of employees, clients, information, and assets.
ESDC is responsible for:
7.1.1
Establishing governance committees to provide formal oversight on the management of ESDC’s security program in order to:
- Set the organization’s security and identity management direction;
- Ensure that the security function is transparent, responsive and effective; and
- Make certain that all matters pertaining to ESDC’s security risk management as well as security operations and administration are aligned and operating according to the program direction of the CSO.
Figure 1 (below) is an organization chart for the Security Program Governance, showing the various executive committees and groups involved the departmental–wide security program.
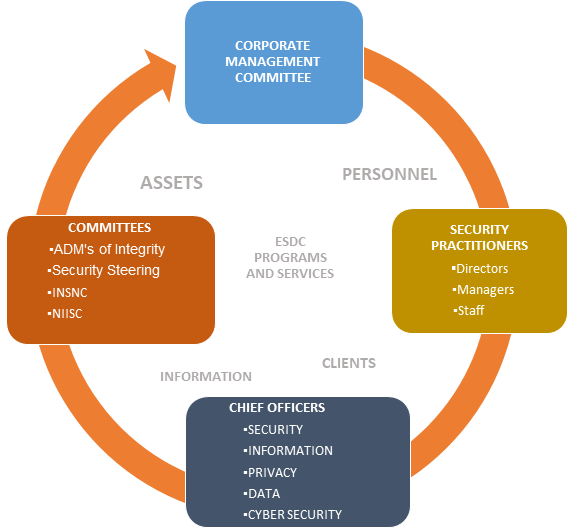
*INSNC – Integrity Services and Security National Committee
**NIISC – National Internal Integrity Security Committee
7.2 Risk identification and mitigation
ESDC’s risk identification and mitigation measures use an evidence-based approach to address pervasive threats, gaps and vulnerabilities that could exist across the Department.
The organization is required to:
7.2.1
Apply advanced analytics to look at trends and to identify and integrate the risks that are within or related to the security program into the broader corporate strategic planning and business continuity planning processes.
7.2.2
Include the Department’s security risks in the Departmental Security Plan for proper assessment, monitoring and tracking of risk mitigation strategies and plans.
7.2.3
Develop and employ analytical tools to help strengthen the Department’s security posture; detect and prioritize threats; and calculate the impact and likelihood of potential events/incidents. This will ensure that risk mitigation activities and plans are based on the assessment and tolerance levels of those risks.
7.2.4
Employ a variety of security risk identification and mitigation measures on an on-going basis including prioritizing and ranking risk levels to guide data-driven decision-making.
7.2.4.1
A Threat and Risk Assessment methodology (TRA) for conducting security assessments must be developed and implemented to include examinations of the appropriateness and effectiveness of measures intended to protect people, information and assets at each ESDC-occupied location.
7.2.4.2
The TRA methodology must be followed consistently and reviewed on a regular basis (e.g. every five years), to manage any emerging threats and risks identified at a regional or national level, or as a result of material changes to the physical work environment.
7.2.4.3
Formalize a nationally-approved process to carry out, monitor, and report on TRA recommendations to resolution must be established and communicated to stakeholders. This will help to improve transparency, prioritization, mitigation, data-driven decision-making, and ensure that recommendations are actioned in a timely and effective manner.
7.2.5
Develop a multi-year Departmental Security Plan. The Plan should be implemented and reviewed annually to assess its effectiveness and appropriateness in achieving the Departmental priorities and objectives including protecting its people and the public they serve, its vast information holdings, its physical assets and the integrity of its services and operations against.
7.2.5.1
The Departmental Security Plan must define controls; detail roles and responsibilities; outline security risks and mitigating strategies; communicate the goals, priorities and timelines for improving the departmental security program.
7.2.5.1
The Departmental Security Plan must specify monitoring activities and reporting requirements. Credible and reliable performance metrics must also be identified to include expected results, indicators, and timeline targets for each security risk area.
7.2.6
Establish and clearly define the purpose and mandate of appropriate Security Steering Committees, chaired (or co-chaired) by the Chief Security Officer and comprised of key departmental stakeholders.
7.2.6.1
Security Steering Committees will plan for, review and monitor security risks, trends, measures and provide oversight of the ESDC security program.
7.2.6.2
The Committees’ mandate should include overseeing Department-wide policy development, collaboration and consultations between NHQ, regional RSO’s and other stakeholders. This includes developing, implementing and maintaining a coherent and integrated security policy suite that meets both the Departmental needs and mandate as well as Treasury Board Secretariat requirements.
7.2.6.3
All security-focused committee decisions must be tracked and consistently follow-up up to conclusion.
7.2.7
ESDC’s insider risk program focuses on internal fraud prevention, leverages intelligence, and maintains practices that continuously monitor and assess risks to prevent the likelihood of insider attacks, unethical behaviour or illegal activities from its employees.
The organization is required to:
7.2.7.1
Develop an insider threat risk strategy that aligns with ESDC’s Corporate Risk Profile, mandate and key priorities.
7.2.7.2
Conduct periodic internal fraud risk assessments to determine areas of vulnerability and continually monitor for changes in the fraud threat environment.
7.2.7.3
Leverage the tools of the security program to develop repeatable processes that monitor, respond, mitigate, track and securely report on unusual behaviours of alleged or suspected acts of fraud by employees. With the emergence of our new work reality, telework and hybrid work this creates new concerns and challenges for the department. In order to continue to adequately protect Canadians, data and information, new measures are being put in place every day. Therefore, a variety of technological solutions, tracking mechanisms and advanced data analytics will be needed to limit threat exposure and to reduce insider incidents.
7.2.7.3.1
Make use of both structured and unstructured data sources to identify and assess risk indicators or to reveal patterns, hidden relationships and anomalies.
7.2.7.3.2
Ensure that all insider threat monitoring practices comply with privacy requirements and that sensitive information is limited to relevant stakeholders only.
7.2.7.4
Establish a breach response program that considers both internal and external breaches as well as accidental and malicious violations.
7.2.7.5
Develop and implement a consequence of management process for cases where fraudulent activity have been confirmed so that all incidents are securely managed in a standardized fashion and involve the right stakeholders.
7.2.7.6
Maintain collaboration and coordination across the department (Security, IT Security, Legal, Privacy, HR) and with other government partners in order to construct a holistic solution to insider fraud and to establish a balanced approach to combatting the threat of insider attacks.
7.2.7.6.1
Develop concise communication protocols in order to build support amongst stakeholders and to develop constructive working relationships in managing these risks.
7.2.7.7
Put measures in place to build and maintain capacity for the insider threat program.
7.2.7.7.1
Maintaining the right skill levels and experience will allow cases to be investigated thoroughly and fairly; the appropriate corrective measures taken; and provide for the prompt deployment of preventative measures.
7.2.7.8
Provide timely and efficient communications to employees on fraud control activities and develop messaging that promote and sustain a fraud awareness environment and increase employee awareness of insider threat risks.
7.2.7.8.1
Employees will be informed and motivated to report allegations or suspicions of fraudulent activities; will gain an understanding of their responsibilities in identifying potential security weaknesses; and will learn what actions to take when these acts are witnessed.
7.3 Personnel security screening
Security screening is one of ESDC’s key security element that enhances the trust between government and Canadians. Anyone who requires access to ESDC information, assets or facilities needs to meet the organization’s security requirements. The level of clearance required is determined by the duties to be performed and the sensitivity of information, assets or facilities that needs to be accessed.
The Department is required to:
7.3.1
Maintain a systematic and consistent approach to security screening, aligned with the Treasury Board’s Standards, to ensure that the ESDC personnel security screening program continues to mitigate the risks surrounding the granting of access to those hired or contracted.
7.3.2
Formalize, fully implement, and monitor security screening procedures and practices.
7.3.3
Appropriately safeguard or dispose of all personal information created, collected, used, disclosed, or retained throughout the screening process in accordance with government standards for privacy and the protection of personal information.
7.3.4
Use established service standards to ensure that all Security screenings are processed in a timely manner.
7.3.5
Inform employees of their security responsibilities and of the consequences of not fulfilling or applying them, once their security status or clearance have been granted or updated.
7.3.6
Consult with the human resources organization when a revocation of clearance is being considered for an employee. The reason for revocation must be documented and individuals must be informed in writing of the decision and of their rights of review or redress.
7.3.7
Put in place a formal monitoring process to assess and oversee the quality of the screening practices being carried out; chart modifications as needed, and ensure that any resulting recommendations are effectively implemented.
7.3.8
Provide periodic reporting, including both quantitative and qualitative information and comparisons against approved performance metrics and service level standards. This will allow senior management to assess the efficiency and effectiveness of the security screening process. Data and data sources used to produce this reporting should be reviewed to ensure the quality and integrity of the information provided.
7.4 Information Technology Security (ITS)
The ESDC Information Technology Security Policy outlines the IT Security governance structures, management practices, objectives, expected results, and requirements to modernize government operations through new technology-based solutions; transform business processes and the delivery of goods and services to consumers.
The Department is responsible for:
7.4.1
Ensuring that IT Security measures cover a range of objectives designed to protect the confidentiality, integrity and availability of information and systems from being adversely impacted due to deliberate or accidental threats, and natural hazards. This includes application of protection mechanisms for data storage devices, end-user computing devices, servers, networks and cloud-based systems that handle data owned or controlled by ESDC.
7.4.2
Addressing the following areas, with coordination between the management of IITB and other branches:
7.4.2.1
Appropriately safeguard or dispose of all personal information created, collected, used, disclosed, or retained throughout the screening process in accordance with government standards for privacy and the protection of personal information.
7.4.2.2
All data under ESDC’s control must be protected according to its level of sensitivity, risk to the Department and third party data protection obligations, regardless of its location or delegated custodians.
7.4.2.3
All end-user devices must be secured with appropriate controls for data protection and access control to ESDC-controlled data and systems.
7.4.2.4
All IT systems operated on-premise or in cloud environments must have measures in place to ensure that critical business processes are supported with active and tested Business Continuity Plans and Disaster Recovery Plans.
7.4.2.5
All information systems must have appropriate levels of event logging and security monitoring capabilities to support the Department’s incident tracking and response processes.
7.4.2.6
All departmental networks must be architected and implemented with security controls that prevent and detect unauthorized access to sensitive data, devices and systems, and which support centralized network security event/incident tracking.
7.4.2.7
All operational systems operated on-premise or in cloud environments must be secured against unauthorized access, and must be kept up to date with security patches and controls to compensate for vulnerabilities, and to report on security events/incidents occurring within systems for security incident tracking and response.
7.4.2.8
All operational systems must undergo security assessments proportional to their level of sensitivity and level of risk to which they may expose the departmental networks, as well as other systems and data, and must have appropriate security controls in place to provide an acceptable level of risk to the Department.
7.4.2.9
All employees must undergo security awareness training and education to ensure that they are able to recognize and avoid threats in their areas of responsibilities, and to report potential threats and vulnerabilities they may encounter to the appropriate authorities for review and potential response.
7.5 Physical security
ESDC’s systematic management of physical security include continuous assessment of risk, threats and analysis and the implementation, monitoring and maintenance of appropriate internal management controls.
ESDC’s physical security measures must allow the Department to identify, escalate and address exceptions where physical security requirements and responsibilities are not being met. As such ESDC must:
7.5.1
Put into place, physical security governance and oversight to ensure the consistent coordination, planning and integration of physical security activities with departmental operations, plans and priorities both at the national and regional levels.
7.5.2
Establish and communicate a physical security strategy and plan that incorporates identifiable elements of protection, detection, response and recovery relating to security threats and risks.
7.5.3
Use an integrated approach to carryout the department’s physical security activities. Ensure that physical security controls remain current to continuously adapt to and address the changing needs of the department and its security environment.
7.5.4
Define, monitor, and report on the physical security standards related to office layouts and the positioning of security equipment and systems, and ensure align with Royal Canadian Mounted Police guidelines and other relevant policy instruments.
7.5.5
Put into place approved action plans for layered threat defense and protection for each ESDC-occupied workplace facility and coordinate with the appropriate stakeholders.
7.5.5.1
Workplace facility considerations and designs must be balanced and flexible to ensure the safety of staff, clients, and the protection of departmental assets and information. This includes having in place mechanisms and products that promote accessibility for all zones except where exclusions exists.
7.5.6
Assess regional disparities in physical security controls to ensure they are applicable and risk-based.
7.5.7
Implement and consistently monitor the standardized Threat and Risk Assessment (TRA) process and methodology as part of the Security Program.
7.5.8
Devise and employ a formal process to monitor TRA completion as well as the implementation of TRA recommendations to reduce the risk of compromise to employees, departmental assets, information and facilities.
7.5.9
Establish an oversight management process (and tools) to detect, respond, correct and report on physical security deficiencies to mitigate associated risks.
7.5.10
Develop and put into practice a reliable system and mechanisms to monitor and report on physical security activities in order to support senior management decision-making.
7.5.11
Employ measures to protect information in its physical form, including assets at rest (for example, in use or in storage) in transit (for example, in transport or in transmittal), and through appropriate destruction, in accordance with their sensitivity and with departmental security practices.
7.5.12 Video surveillance
The practices surrounding the installation and the use of video surveillance, as a standard security tool, are tailored to enhance the safety of individuals and for the protection of departmental premises and other valuable assets.
Given that employees and the public have a right to the reasonable expectation of privacy in certain areas, the management practices for the use of video surveillance systems includes respecting ethical considerations and maintaining the integrity of the intended purpose.
Therefore, the use of a video surveillance system must support the mandate of the Department and must:
7.5.12.1
Align the installation, use, and maintenance of the security video surveillance system (SSVS) with departmental security standards and policies as well as affiliated Acts and legislations.
7.5.12.2
Avoid using the security video surveillance system for administrative purposes such as, but not limited to, a means to record employees day-to-day activities for possible disciplinary and or other non-security related matters.
7.5.12.3
Not install SSVS in areas where there is an expectation of privacy consistent with the Privacy Act and the Canadian Charter of Rights and Freedoms.
7.5.12.4
Inform all individuals who could be recorded by a SSVS on the collection and use of personal information in accordance the provisions of the Privacy Act and/or the Access to Information Act.
7.5.12.5
Ensure that video surveillance systems are not set up to follow the movements of specific clients, employees, or individuals except in special emergency circumstances as approved by the CSO.
Additional information on security video surveillance can be found at the following : Departmental Security Policies and Reference Tools
7.6 Business continuity management
The continuity of key business operations is foundational for the organization to successfully deliver its mandated programs and services to Canadians. The CSO and the Chief Information Officer (CIO) work together to provide coordination of the organization’s continuity or recovery of critical services and activities in the security environment.
The Department must:
7.6.1
Fully establish and maintain a BCP Program governance structure and associated practices to enable the organization to focus its limited resources on its most critical functions.
7.6.2
Carry-out Business Impact Analysis to identify and prioritize critical services, critical support services, functions and associated assets.
7.6.3
Develop and regularly update Business Continuity Plans (BCPs) and IM/IT recovery plans for all identified critical services and critical support services (national and regional). A test cycle for these plans must be put into place to ensure that the department can carry out critical services and critical support services during a disruption.
7.6.4
Ensure that the necessary resources, infrastructure and tools are in place and matched with the appropriate mechanisms to support critical services and critical support services. In order to minimize the consequences of disruptions for staff and services, ESDC must also consider alternative working arrangements (i.e. telework) and accessibility concerns.
7.6.5
Document, communicate and continue to create training and learning programs to promote consistent understanding of recovery practices as well as clarifying roles and responsibilities that direct and report on BCPs.
7.6.6
Document, communicate and continue to create training and learning programs to promote consistent understanding of recovery practices as well as clarifying roles and responsibilities that direct and report on BCPs.
7.6.7
Maintain an appropriate level of readiness through coordination and monitoring of unusual circumstances including cybersecurity preparedness (i.e. using cloud computing and Artificial Intelligence). This involves annual testing, ongoing reviews and revisions of BCP and IM/IT plans as well as developing targets for capacity building.
7.6.8
Periodically report results of BCP activities and the state of the program to the appropriate ESDC governance committees.
7.7 Emergency management
"Emergency Management is the prevention and mitigation of, preparedness for, response to, and recovery from emergencies”
- Emergency Management Act
ESDC is responsible for the protection of its employees, clients and assets. Within the department, comprehensive and integrated emergency management practices are a shared organizational responsibility and is embedded in the planning process throughout the organization.
The organization must:
7.7.1
Maintain a high level of readiness for ESDC’s emergency management practices by defining clear roles and responsibilities; coordinating departmental activities with partner departments and agencies; as well as developing and testing (on a regular basis) an updated and approved emergency management and response plan.
7.7.2
Establish and maintain a multi-layered governance structure for emergency management as a platform to discuss mandate-specific emergency management to achieve a well-informed and fulsome departmental response to multiple simultaneous or large-scale emergencies.
7.7.3
Establish a formal process and common criteria to develop, maintain, and/or discontinue strategic emergency management plans based on all-hazards risk analysis. This process must ensure that the plans are aligned and must include a robust risk assessment methodology to address mitigation/prevention, preparedness, response and recovery from major emergencies.
7.7.4
Seek out and maintain adequate capacity and flexibility, including a skilled emergency responder inventory and a national inventory of equipment, to meet the goals outlined in the emergency management plans in order to continue operating during emergencies and quickly recover from disasters.
7.7.5
Develop written procedures for emergency response and training material for security practitioners, responders and departmental personnel.
7.7.6
Conduct regular training exercises involving both internal and external stakeholders in order to ensure that the emergency management plans functions as intended.
7.7.7
Develop notification procedures and protocols to communicate technical advice and direction to branches and regions with respect to emergency management.
7.7.8
Use an integrated approach to monitor and provide information on emergency management issues and the state of readiness for the organization’s emergency management system.
7.7.9
In collaboration with key federal partners, conduct periodic and comprehensive reviews of the emergency management plans based on a risk management approach.
7.7.10
Contribute to the federal government’s all-hazards response plan and harmonization of efforts through the effective maintenance and management of the National Emergency Operations Centre (NEOC).
Note 1: Figure 1 above outlines the Security Program’s governance structure includes the various committees where Emergency Management activities are discussed, considered, and approved.
7.8 Information management
ESDC safeguards one of the largest repositories of personal information on Canadians in the federal government. The Department recognizes that information is a strategic asset that is essential to the effective delivery of the organization’s mandate. Its effective management further maintains a foundation of trust between government and Canadians.
As such, ESDC is responsible for:
7.8.1
Ensuring that the usefulness and appropriateness of the information management organizational structure are assessed and reviewed to clarify authorities as well as responsibilities. These measures will also enable accountability and foster effective data-driven decision-making processes.
7.8.2
Managing information in accordance with regulations and best practices so that it is accessible and meaningful for those who need to use it to carryout their duties.
7.8.3
Establishing and monitoring appropriate security measures that guide those who access protected data or the GoC’s most sensitive information. This includes personnel security screening activities and protocols as well as other measures that prevent unauthorized access to telecommunications traffic, or to any written information that is transmitted or transferred.
7.8.4
Developing and maintaining processes and practices to monitor that the identification and marking of sensitive information is compliant with policy and that appropriate safeguarding measures are considered at all times during the lifecycle of the information.
7.8.5
Leveraging existing and new technologies to protect against loss, damage, unauthorized access, interception, alteration, or destruction of information.
7.8.6
Providing employees with IM training, awareness, tools and guidance to carryout their roles effectively, while safeguarding information at all times.
7.8.7
Developing, implementing, and monitoring mechanisms that measure and assess the overall compliance and performance of the Department’s IM program. This includes having formal mechanisms to obtain input and feedback from users on IM systems, tools, training and awareness initiatives
7.8.8
Furnishing oversight committees with periodic reports on information management activities, protocols as well as any threats to the protection of sensitive information and data.
7.9 Communications security
ESDC’s communications security (COMSEC) objectives include preventing unauthorized access to information and data derived from telecommunications; ensuring the authenticity of such telecommunications; and assuring the protection of classified and protected information and data.
The organization is responsible for:
7.9.1
Ensuring that COMSEC custodians are up-to date with their training prior to administrating COMSEC sub-Account duties, given the evolution of technology and the increase of data and security risks.
7.9.2
Maintaining and periodically updating the Information Technology (IT) systems in order to accommodate storage and use cryptographic keying material.
7.9.3
Ensuring that the facilities that are being used are secured/approved according to the proper safeguarding requirement for Accountable COMSEC Material (ACM).
7.9.4
Safeguarding office areas so that, at a minimum, the area is protected to the highest classification of equipment when keyed.
Note 2: The use of GCSI (Government of Canada Secret Infrastructure) can support the processing of secret level information given the movement to a more digitalized world, a paperless environment, a co-working environment and the need to know principle.
7.10 Privacy practices
Because of its information holdings as well as its use and disclosure of personal information, ESDC is subject to Treasury Board’s privacy policies and directives as well as the requirements of the Privacy Act and the Department of Employment Department of Employment and Social Development Act.
ESDC is responsible for:
7.10.1
Maintaining close collaboration between ESDC’s Security and Privacy Management units to define and communicate personal information safeguarding expectations to the Department.
7.10.1.1
The department must clearly identify employee positions that are authorized to access, use or disclose personal information and under what circumstances.
7.10.2
Supporting Increased awareness, promoting best practices in personal information stewardship, and demonstrating a sustained commitment to safeguarding personal information through support for and endorsement of mandatory training.
Note 3: For additional direction on the collaborative efforts and management of privacy breaches, refer to SIMU and PMD policy and processes.
Note 4: New or modified activities that involve personal information benefit from the collective scrutiny through the collaboration of departmental partners and stakeholders in executing their respective security-related responsibilities.
7.11 Security event management
ESDC personnel tackle a variety of security events including internal incidents, natural disasters, and incidents involving national security. With the diversity of events that can occur, the Department investigates and acts when significant issues arise, takes appropriate remedial actions to address these issues, and put measures in place to future occurrences.ESDC must:
7.11.1
Ensure that a national risk-based approach is developed for both corporate and regional security incident management and threat detection.
7.11.2
Use modernized technology to implement measures that ensure security events/incident responses are triggered in real-time for disruptions that affect the Department.
7.11.3
Formalize roles and responsibilities and coordinate security event management processes with communications plans, business continuity, emergency management, strike management, and other contingency plans and measures, as applicable.
7.11.4
Inform other departments and stakeholders when there is reason to believe that an event/incident originated from, or could potentially affect, an organization, including internal enterprise service organizations, departments that provide or receive services under agreements or other arrangements, suppliers and other partners.
7.11.5
Coordinate readiness processes and measures with security event management processes, business continuity plans, and with emergency preparedness and response measures.
7.11.6 Accessibility
Security practices are employed to act as barriers to protect an organization’s personnel, clients and assets. However, unintended consequences may result in creating barriers for persons with disabilities; those wanting to gain access to ESDC’s programs and services; and for the organization’s personnel who need seamless processes to carryout their daily duties.
The organization must:
7.11.6.1
Proactively include accessibility considerations that support the full participation of all persons in the work environment in the organization’s security practices.
7.11.6.2
Incorporate legal requirements and workable security-related alternatives for accessibility into the organizations decision-making as well as its emergency response and physical security plans.
7.11.6.3
Develop, adopt, report, and regularly review security standards and guidance to optimize accessibility considerations.
Note 5: IT Security and privacy practices relating to accessibility to systems, programs and services in ESDC’s digital environment is further outlined in the organization’s Accessibility Policy.
7.12 Internal security inspections and investigations
ESDC’s management practices for (planned and periodic) internal inspections and investigations include outlining how inspections and investigations into alleged or suspected employee misconduct are to be conducted; defining performance measures; and charting how inspection or investigative information is to be ultimately leveraged while respecting employees’ rights.
The Department is responsible for:
7.12.1
Ensuring that the organization’s inspections and investigations are based on up-to-date risk assessments, analysis of security trends, and are carried out in a fair, consistent, and unbiased manner. They are to be completed in order to:
- Evaluate the security protocols, practices, controls for inspections and internal investigations into alleged or suspected employee misconduct;
- Uncover any potential risks for the organization; and
- Provide senior management with action-oriented recommendations for corrective actions to support their decision-making.
7.12.2
Clearly defining and documenting the roles and responsibilities of practitioners who carryout inspections and investigations. These requirements are regularly reviewed and updated.
7.12.3
Providing security inspectors and investigators with access to the appropriate tools and systems (with enhanced reporting capabilities) to support their work and to facilitate workflow management and tracking processes.
7.12.4
Formalizing and communicating national standardized procedural documents so that inspections and investigations documented and are carried out in a fair, consistent and transparent manner. Ensure these tools are regularly updated, approved and made available to staff through a centralized repository, (or if of a sensitive nature) on a need to know basis.
7.12.5
Including clear, concise, and fact-based findings and recommendations in each inspection and investigation report. This will support the collective knowledge of security practitioners as well as support senior management’s decision-making.
7.12.6
Putting into practice a formal monitoring process to assess and oversee the quality of the inspections and investigations being carried out; chart modifications as needed, and ensure that any resulting recommendations are effectively implemented.
7.12.7
Developing and promptly communicating periodic reports that include both quantitative and qualitative information as well as comparisons against approved performance metrics and service level standards to appropriate senior management.
7.12.8
Reporting promptly to the appropriate law enforcement authorities where there are reasonable grounds to believe that an employee’s conduct may be illegal or criminal.
7.12.9
Conducting periodic reviews of the data and data sources used to produce inspection and investigative reports to ensure the quality and integrity of the information provided.
Note 6: For information pertaining to ESDC’s IT-related inspections that address design, code, deployment, and monitoring, please consult the Information Technology Policy.
Note 7: Need to Know Principle - Limiting access to sensitive information to individuals allows for access to information necessary for one to conduct one's official duties and includes providing information to anyone that the people with the knowledge consider necessary to share it with. In order to achieve confidentiality, consideration must also be given to maintaining the integrity of sensitive information especially in situations where employees with varying need to know requirements.
7.13 Security in contracting
The Department assesses and identifies security requirements relating to all stages of the contracting process and ensures successful contractors and their firms to go through the required security screening processes to determine their reliability and trustworthiness to access government information and assets.
ESDC is responsible for ensuring that:
7.13.1
Relevant security controls are implemented and consistently monitored at all stages of the contracting process, whether the Department uses its own internal contracting process or the (PSPC) Industrial Security Program.
7.13.1.1
The Industrial Security Program is to be utilized in situations where a contract involves access to sensitive information and assets above the organization’s approved contracting authority.
7.13.2
The Security Requirements Check List (SRCL) which is used to determine the conditions and requirements of the department for the internal contracting process are met. According to the list of requirements, contractors and their firms cleared to the appropriate security levels.
7.13.3
The security requirements for a contract are validated prior to the start of the contract or the contractor being provided with physical access to facilities, information or assets.
7.13.4
Periodic reviews of contract files are carried out as part of the department’s quality assurance program to verify that the files meet the security in contracting requirements.
7.14 Security awareness and training
ESDC employees are provided with accessible, innovative security-tailored awareness and continuous learning opportunities so that they understand and comply with their security responsibilities and contribute to building a strong security culture.
The organization must:
7.14.1
Develop and implement a structured training approach as well as a professional development program for security practitioners (national and regional). This will support the development and mobility of the analysts who carry out the various security-related activities, promote retention and assist with career development.
7.14.2
Ensure that security practitioners undertake the necessary training to carry out their daily activities as it relates to their specific roles and security responsibilities. This training will allow them to be better:
- Positioned to resolve complex security issues and respond to new security threats;
- Able to proactively implement security measures and controls within the organization in accordance with ESDC and TBS Security policies and directives. They will also be able to weigh the consequences of any actions;
- Equipped with tools and security practices to ensure effective coordination and interaction with their departmental, government-wide colleagues and private sector; and
- Provided with a working environment, a career pathway and a distinct set of competencies in order to attract and retain these professionals.
7.14.3
Ensure that all employees take part in awareness activities, continuous learning opportunities, and remain current with mandatory security training (protocols, tools, and systems) so that they are:
- Made aware of the key security controls measures, which aim to prevent, detect and respond to security risks, threats and/or events; and
- Prepared to carryout requirements outlined in security policies and directives while maintaining vigilance to identify and report security incidents.
7.14.4
Develop and implement standardized processes and practices for providing security travel briefings to employees traveling to, and/or working remotely from, international locations.
7.14.5
Make use of Government of Canada travel site and other open source intelligence platforms to provide information about safe travel including the protection of information and assets when employees are on department-mandated travel.
7.14.5.1
Consideration must be given to the risk levels associated with travel warnings and alerts, infectious decease advisories, and general recommendations for caution while travelling to specific foreign locations.
7.14.5.2
Security travel briefings must also include information on how to get assistance should an emergency situation occur while travelling abroad.
7.14.6
Conduct periodic reviews of the security training and awareness program in order to identify and prioritize security-training needs; observe and apply current security trends and threats/risks, while providing employees with the appropriate tools, practices, and protocols.
8. Roles and reponsibilities
The management of security intersects with other ESDC branches, management functions, the ESDC Labour Program, as well as other government organizations. The Department is structured to manage the security program across five regions with each employee’s role and responsibility linked to the ESDC Code of Conduct.
The organization must:
8.3
Details of roles and responsibilities are outlined in Annex B below.
10. Resources
ESDC is committed to align resources with risk levels and allocate resources strategically so that employees, while working on the right things to meet the organization’s mandate, are also considering their security responsibilities.
ESDC must:
10.3
Put in place a dedicated, full-time security officer (RSO) for each region and ensure that RSO responsibilities do not result in the splitting of duties across a given region or use of external resources is not put into practice to conduct facility security assessments, personnel screening and other security activities.
10.5
Include Security controls in ESDC’s standard staff on-boarding and separation processes and practices so that managers and employees are aware and kept up-to-date on key aspects of their security responsibilities and reduce critical risks to the integrity of the organization’s security posture.
11. Quality assurance and continuous improvement
Having a Quality Assurance and Continuous Improvement Program can provide the organization with added opportunities to prevent and mediate internal and external risks/threats, meet its objectives, and better serve Canadians.
The Department is required to:
14. Non-Compliance, Consequences
The consequences of an ineffective security program may include unnecessary risks to the personal safety and security of employees and clients; the compromise of sensitive information; the loss of departmental assets, and ultimately, a loss or reduction of public confidence in the department's ability to manage its security program and deliver its services to the public.
As such, non‐compliance with this Policy and its related standards will be treated as a serious matter. ESDC employees who violate this Policy may be subject to administrative actions up to and including termination of employment. Non‐ESDC personnel who violate this policy may have their access revoked, and may be subject to legal action.
16. References
ESDC and Government of Canada policies, directives, standards and other documents relevant to this Policy are identified in Annex C.
17. Enquiries
All enquiries relating to this Security Policy and any future amendments may be directed to Director General, Internal Integrity and Chief Security Officer
Revision History
Caption text Version Number Description Date Modified Author(s) 1.0 Initial approved version June 2021 Judith Wilson and Gloria Mukendi Annex A – Security Controls
Security screening must be conducted in a way that is effective, rigorous, consistent and fair to provide reasonable assurance that individuals can be trusted to safeguard ESDC’s information and assets and can reliably conduct their work duties, and to enable transferability of security screening between departments.
Information technology security requirements, practices and controls must be defined, documented, implemented, assessed, monitored and maintained throughout all stages of an information system’s life cycle to provide reasonable assurance that information systems can be trusted to adequately protect information, are used in an acceptable manner, and support ESDC’s programs, services and activities.
Physical security requirements, practices and controls must be defined, documented, implemented, assessed, monitored and maintained throughout all stages of the real property and materiel management life cycles to provide reasonable assurance that individuals, information and assets are adequately protected, thereby supporting the delivery of the organization’s programs, services and activities.
Business continuity management must be conducted systematically and comprehensively to provide reasonable assurance that in the event of a disruption, the department can maintain an acceptable level of delivery of critical services and activities, and can achieve the timely recovery of other services and activities.
Information management security requirements, practices and controls must be defined, documented, implemented, assessed, monitored and maintained throughout all stages of the information life cycle to provide reasonable assurance that information is adequately protected in a manner that respects legal and other obligations and balances the risk of injury and threats with the cost of applying safeguards.
Security requirements in contracts and other arrangements must be are identified and documented, and related security controls must be implemented and monitored throughout all stages of the contracting or arrangement process to provide reasonable assurance that information, individuals, assets and services associated with the contract or arrangement are adequately protected.
Security event management practices must be defined, documented, implemented and maintained to monitor, respond to and report on threats, vulnerabilities, security incidents and other security events/incidents, and ensure that such activities are effectively coordinated within the department, with partners and government-wide, to manage potential impacts, support data-driven decision-making and enable the application of corrective actions.
Security awareness and training must be conducted systematically and comprehensively to ensure that individuals are informed of their security responsibilities and maintain the necessary knowledge and skills to effectively carry out their functions, and to provide reasonable assurance that individuals will not knowingly compromise security and that they understand the potential consequences of not meeting their security responsibilities.
Annex B – Roles And Responsibilities
Internal
- Deputy Head
- Responsible for ensuring that their branches/organizations adhere to the Policy.
- Chief Security Officer (CSO)
- Appointed by the Deputy Head, is responsible to develop, implement, maintain, and monitor security risk management processes to meet security controls, , and to continuously adapt the processes to the changing security needs of ESDC. The CSO must also ensure the Communication, collaboration and planning of physical security activities between NHQ, RDGs, and regional RSO functions.
- Chief Information Officer (CIO)
- Ensures the effective and efficient management of the Department’s information and technology assets. The CIO and the CSO work together to ensure that appropriate security measures are applied to all departmental information and technology assets, activities and processes.
- Chief Privacy Officer (CPO)
- Is the Department’s functional authority on all privacy matters.
- Chief Data Officer (CDO)
- Leads and manages the development of an enterprise-wide data strategy to optimize the use of ESDC’s data assets
- Designated Official for Cyber Security (DOCS)
- Responsible for assessing the impacts and mitigating actions in response to cyber security events/incidents and ensuring that cyber security requirements and appropriate measures are being applied in a risk-based, lifecycle approach to protect IT services. The DOCS also ensures that departmental plans, processes and procedures are in place for responding to cyber security events/incidents and reporting of incidents to the appropriate authorities and affected stakeholders, in accordance with the Government of Canada Cyber Security Event Management Plan.
- Chief Financial Officer (CFO)
- Accountable for corporate financial planning and performance monitoring; sound stewardship of corporate investments; strategic procurement; corporate accounting, external and management reporting; asset management and business shared services for ESDC.
- Chief Audit Executive
- Responsible for providing the Deputy Minister of ESDC with independent and objective assessment and assurance on the effectiveness and adequacy of risk management, control and governance processes within the Department.
- Regional Director Generals
- Establish and advance the regional strategic direction for business transformation, risk management and program delivery.
- Regional Security Officers (RSO)
- Support the delivery of the security program in their respective regions and participate in the national development and implementation of the security program including policies, directives, standards and tools.
- Directors and Managers
- Ensure that their employees comply with the Security Policy and effectively apply security practices in day-to-day operations. They must put into places practices and protocols to ensure the protection of employees and safeguarding the information, assets and services for which they are responsible.
- Security practitioners
- Ensure departmental security activities are coordinated and integrated while supporting and providing the CSO with recommendations for deficiencies identified in performance measurement and evaluations. Security practitioners must also provide expert advice on the application and effectiveness of security controls related to their area of responsibility.
- All employees
- Must familiarize themselves with the security Policy and comply with all Government of Canada and departmental security-related tools and reference material. They must promptly report suspected or actual security violations/incidents or instances of non-compliance, unusual or suspicious activity and other possible security risks or gaps to their supervisor or manager.
- All ESDC Branches
- Each branch must ensure the integration of this policy in their strategic and operational planning in order to provide maximum alignment of programs and operational policies across the Department.
- Innovation, Information and Technology Branch
- The activities of the Innovation, Information and Technology Branch (IITB) establishes guidelines for the prevention of intentional and/or accidental threats to departmental valuable assets, systems and facilities and mitigates the risks of unauthorized disclosures, removal and/or modification of sensitive information.
- Corporate Secretariat
- The Corporate Secretariat branch is responsible for the Department’s access to information program, issuing and managing privacy management policy, the provision of privacy advice and guidance, and for privacy operations in the National Capital Region. The branch’s Privacy Management Division (PMD) is the Department’s Centre of Expertise for privacy advice. PMD supports the horizontal implementation of the Department’s privacy policies and initiatives, conducts risk analysis including privacy impact assessments, and delivers privacy compliance advisory services for ESDC;s programs.
- Internal Audit
- Internal Audit reports on the adequacy of internal controls, the accuracy of transactions, the extent to which assets are accounted for and safeguarded, and the level of compliance with departmental and government-wide policies and regulations.
- Human Resources Services
- As one of ESDC’s enabling services branches, Human Resources Services Branch (HRSB) is responsible to support the Department’s business and mandate by providing policies, programs and services to build capacity, foster retention and development of an engaged workforce and a healthy workplace and culture that supports the strategic direction of the organization.
- Financial Services
- Financial Services provides centralized financial management and comptrollership advice and support to the Department’s branches to transform their day-to-day operations and the delivery of programs and services.
- Legal Services
- Provides legal services to support the programs, operations and key initiatives, including legislative and regulatory initiatives for of ESDC.
External
- Treasury Board Secretariat
- Establishes and oversees a whole-of-government approach to Security management as a key component of all management activities by ensuring the conduct of periodic reviews of the effectiveness of security support services, to provide assurance that they continue to meet the needs of departments and the government as a whole.
- Public Safety Canada
- Provides operational leadership for the coordination, information sharing and situational awareness relating to security events/incidents involving multiple GC Departments or Agencies that may have government-wide, intergovernmental, critical infrastructure or national impacts.
- Public Service and Procurement Canada
- Provides leadership and coordination of activities to help ensure the application of security safeguards through all phases of the contracting process within the scope of the industrial security program (ISP). It also provides services related to physical security respecting the PSPC Real Property Program and common services related to IT security for increased efficiency and economy of the GC.
- Shared Services Canada (SSC)
- Responsible for the planning, designing, building, operating and effectively maintaining efficient and responsive enterprise IT security infrastructure services in order to secure the Government of Canada data and systems under its responsibility.
- Other Lead Departments
- Lead security agencies provide advice, guidance and services to support the day-to-day security operations of departments and enable government as a whole to effectively manage security activities, coordinate response to security incidents, and achieve and maintain an acceptable state of security and readiness. Additional information relating to the roles of lead department is found in section 5 of the PGS.
- Agents of Parliament
- Agents of Parliament carry out duties independent from government and support Parliament in its government oversight role by reviewing the implementation of legislative measures and by acting as monitors and ombudspersons on behalf of citizens.
- Consultants and contractors
- While under contract with ESDC, consultants and contractors are bound by the security conditions outlined in contractual documentation; must abide by the requirements of this Policy; and are accountable to the CSO on all matters relating to security
Annex C – References
Legislation
- Access to Information Act
- Canada Labour Code
- Canada Occupational Health and Safety Regulations
- Canadian Charter of Rights and Freedoms
- Accessibility Canada Act
- Criminal Code
- Emergency Management Act
- Financial Administration Act
- Official Languages Act
- Privacy Act
- Public Service Employment Act
- Federal Public Sector Labour Relations and Employment Board Act
- Security of Information Act
- Security of Canada Information Sharing Act
Government of Canada
- Contracting Policy
- Foundation Framework for Treasury Board Policies
- Framework for the Management of Compliance
- Framework for the Management of Risk
- Policy on Information Management
- Policy on Investment Planning: Assets and Acquired Services
- Policy on Management of Information Technology
- Policy on Management of Materiel
- Policy on the Management of Projects
- Policy on Management of Real Property
- Policy on Occupational Safety and Health
- Policy on Results
- Policy on Service
- Policy on Service and Digital
- Values and Ethics Code for the Public Sector