Application Control Questions and Answers
What is Application Control?
Application Control is the practice of using security tools to allow only authorized applications to execute on the desktop.
Why is this technology being implemented within the Department?
ESDC is introducing this technology to help mitigate the risk of phishing and ransomware within the departmental electronic network. The primary goal of this technology is to protect our ESDC electronic network from potentially harmful applications and software by blocking viruses, spyware, ransomware, and other malicious software since they will not be on our departmental list of authorized applications.
How does Application Control work?
Once fully implemented, IITB will establish departmental authorized and, unauthorized lists as well as increased File Protection capability.
Authorized Applications – A list of authorized applications will be developed detailing what is permitted within the Department. Unknown applications which have never been authorized to run will be blocked.
Unauthorized Applications - Known, unwanted, applications can be blocked from executing by individually adding them to the unauthorized list.
File Protection – This technology will also block cybercriminals from making changes to system files (a common hacking tactic).
What will be monitored with this technology?
Initially, this technology will observe what applications/software is being run on the computer. This will allow IITB to monitor and report on applications and software that would have been blocked had Application Control been enabled.
After a period of observation, the technology will be fully enabled and therefore will only allow applications/software that are authorized within the Application Control tool to run on the computer.
What will an employee see when Application Control is installed?
The vast majority of employees will never even know the tool exists; it functions in the background and is not visible while it monitors workstation activity. However, if malicious or unauthorized software tries to run, the software will be blocked, a desktop notification (see below) will be generate and briefly displayed in the bottom right hand coener of the taskbar and IITB will be informed for follow-up.
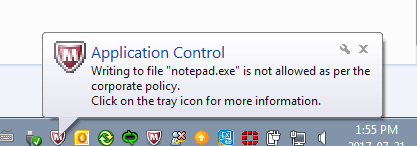
There are also instances when employees may receive the notification when they haven’t attempted to install anything or run unauthorized software. In these instances, the pop-up may be displayed because the Windows operating system is running software in the background, which may trigger the notification.
What does an employee do if they receive the notification pop-up?
If an employee receives the notification and it is not impacting their ability to work, there is no action required.
Employees may be contacted with next steps if it has been determined that their computer is potentially at risk of harmful applications/software or if more information is required.
How do employees know which software or applications they are permitted to use?
The introduction of this technology does not change the existing policies in place for installing software/applications. 90%+ of required Departmental applications are either already installed on devices or can be requested by submitting an online request to the National Service Desk. A good rule of thumb is if employees feel they need to install an application manually, to stop and consider if the application is really required or if other options are available. More information can be found in the Software/Application Service section on iService.
The existing processes and policies also continue to apply for the approval and acquisition of new software that has not yet been approved by the Department.
Please refer to the links below for additional information available on:
When will this be implemented?
It is anticipated that the full implementation will begin in the Fall of 2017.
Who do I contact if I still have questions?
Please submit a service request with the National Service Desk if you have further questions on Application Control.